Monitored Users Report
Enzoic for Active Directory v3.6
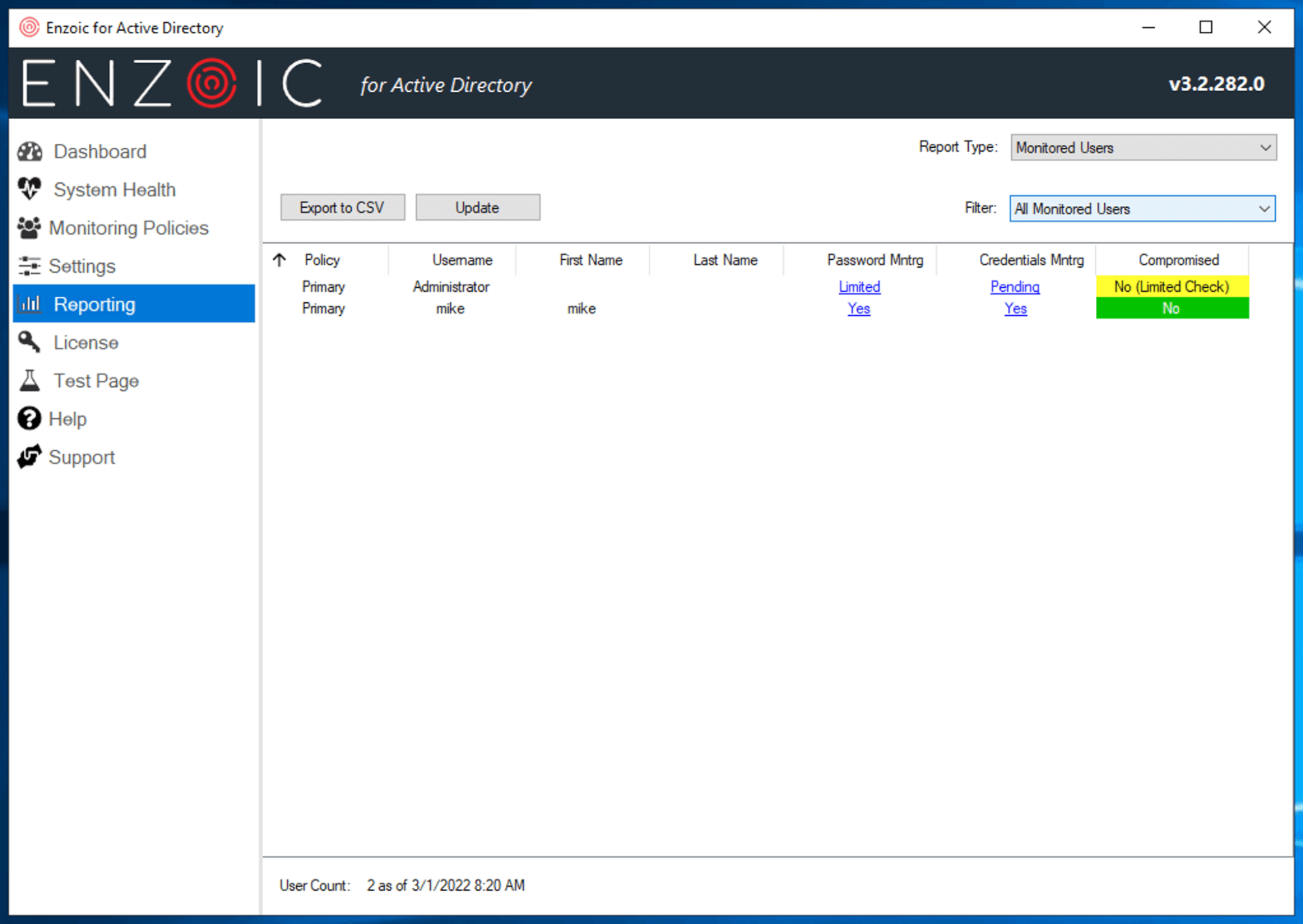
This report shows you a list of all the users currently being monitored by Enzoic for Active Directory, along with a Compromised status for each user. For each user, you can also see what the current status is for Password Monitoring and Credentials Monitoring. The filter dropdown at the top right allows you to further filter the report, so you can, for instance, just see users with currently compromised passwords. The Update button in the header allows you to refresh the report. Since this report can be time-consuming to generate for larger domains, it is only refreshed on demand. If the data is stale (more than 15 minutes out of date), you will see a red warning message next to this Update button reminding you that you need to regenerate the report to see current data.
Monitored Users Report Fields
Policy
The current effective monitoring policy for this user.
Username
The user’s username in AD.
First Name
The user’s first name in AD, if present.
Last Name
The user’s last name in AD, if present.
Password Monitoring
Indicates whether Password Monitoring is active for this user. Possible values are Yes, No, or Limited. Limited checks are used when Enzoic has not observed a password change for this user to cache their current password for more extensive monitoring checks and indicate only an exact match with the user’s current password would be caught (i.e. things like fuzzy matching won’t work). Force a password change for this user to rectify this condition.
Credentials Monitoring
Indicates whether Credentials Monitoring is active for this user. Possible values are Yes, No, or Pending. Pending indicates Enzoic has not observed a password change for this user to cache their current password. Until then, we will not be able to monitor this user’s credentials for compromise. Force a password change for this user to rectify this condition.
Compromised
The user’s current compromise status. See possible status values in the section below.
Compromise Status Values
The potential values for the Compromised column are as follows:
Password Compromised
Indicates this user’s password was found to be compromised during a Password Monitoring scan.
Credentials Compromised
Indicates this user’s credentials (exact email/password combination) were found to be compromised during a Credentials Monitoring scan.
No (Limited Check)
Indicates that while the user’s current password and credentials are not known to be compromised, currently a limited check is being used. A limited check indicates that we do not have the exact password cached, so only an exact match with a compromised password would be flagged. Limited checks are used when Enzoic has not observed a password change for this user to cache their current password for more extensive monitoring checks. Once this user changes their password, the Limited restriciton will be removed.
No
Indicates the user’s password and/or credentials are being checked completely and no compromise has been identified.
Was this helpful?